What is Encryption?
Basically, Encryption is the process transforming data or information into a code, especially to prevent unauthorized access.
It is generally used to protect sensitive information so that only authorized parties can view it.
Simply,when sending a message without encrypting anyone can read the stuffs which includes that message.
In this scenario, Scully is the sender and Mulder is the receiver and the Alien is the is the 3rd party who does not have a authorized to read this message. Scully didn't encrypt the message before sending it to the Mulder. So Alien can read the message.
We can divide Encryption into two main parts.,
- Symmetric Encryption
- Asymmetric Encryption
Symmetric Encryption
Symmetric encryption algorithms are best known as shared-secret key algorithms. The cryptography key is using for both encryption of Plain Text and decryption of Ciphertext.
- The usual key length is 80 to 256 bits.
- A sender and receiver must share a secret key.
- They are usually quite fast (wire speed), because these algorithms are based on simple mathematical operations.
- Examples of symmetric encryption algorithms are DES, 3DES, AES, IDEA, RC2/4/5/6, and Blowfish.
Simply we can describe symmetric encryption in this way...
Asymmetric Encryption
Asymmetric encryption algorithms characteristics include:
- Asymmetric encryption algorithms are best known as public key algorithms.
- The usual key length is 512 to 4,096 bits.
- A sender and receiver do not share a secret key.
- These algorithms are relatively slow, because they are based on difficult computational algorithms.
- Examples: RSA, ElGamal, elliptic curves, and DH.
In Asymmetric Encryption both the sender and the receiver has pair of keys call Public Key and the Private Key. Public Key is a key that anyone can get. But the Private Key is a unique key which only known by the owner (Sender or the Receiver). When encrypting a plain text via Sender's Public Key, the receiver can decrypt that message only through by Sender's Private Key. If some message encrypted from Receiver's Public Key, that message can only decrypt by Receiver's Private Key. Likewise when some message encrypted in Sender's or Receiver's Private Key, it can decrypt only by Sender's or Receiver's Public Key. Here is a simple example for Asymmetric Encryption...
I have implemented simple Encryption / Decryption software to hide the content of your "Text (.txt)" files. I used AES 128 bit Algorithm to encrypt data in your text files. And here is the link to download that software..
https://github.com/janitha1st/Encryption-Decryption-Software-Application
This software is implemented using NetBeans IDE 8.1 and the Language is Java.
- This is the main interface of my Software.
- First you have to give the path to the text file that you need to encrypt. Here "Hello_Cyber" is my text file and it placed in Desktop.
- After you select the path then click the "Encrypt" button and it'll display a message if it was successful.
- After encrypting if you go to the same text file you can see the content like above. It means it was successfully encrypted.
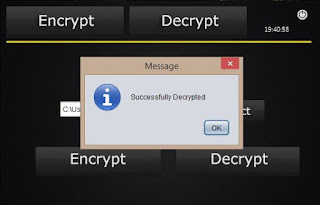
- After encrypted select the path as done before and click the "Decrypt" button. Then it'll display a message if it is success.
- Then you can get the same content which was there before you encrypt the file.
- Specially you should add org.apache.commons.io.jar JAR file to your project. It is also include in my github repository.
Visit my GitHub by clicking : https://github.com/janitha1st/Encryption-Decryption-Software-Application
Hope you guys understand my blog blog. If you have any doubt please send me a mail to janitha.bhakthi93@gmail.com.
Thank You! ;)
Thank You! ;)